Security vulnerabilities have an interesting problem: they’re excellent at being found, but terrible at being fixed.
GitHub just addressed this with two significant updates: security campaigns for secret scanning alerts and assignable alerts for both code scanning and secret scanning. But beneath these practical improvements lies a deeper question about human nature and responsibility.
Why do we need to assign security vulnerabilities to specific people for them to get fixed?
What’s new in security management#
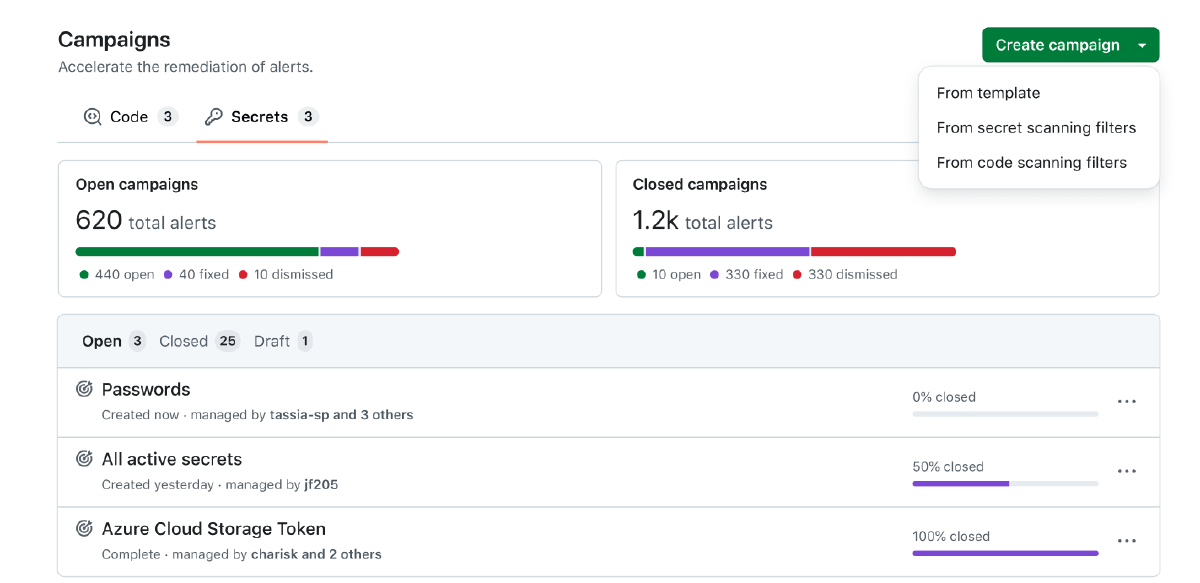
🎯 Security campaigns for secret scanning#
Building on the existing code scanning campaigns, you can now create coordinated remediation efforts for exposed secrets across your organization:
- Centralized tracking of high-impact secrets across repositories
- Campaign progress visibility that reduces fragmented ownership
- Focused remediation on what actually matters most
👤 Assignable alerts for all security scanning#
Both code scanning and secret scanning alerts can now be assigned directly to individuals:
- Clear ownership of specific security issues
- Integrated tracking within GitHub’s development workflow
- Accelerated remediation through personal accountability
The psychology of security ownership#
Here’s what’s fascinating: we can automate the discovery of thousands of security vulnerabilities, but we still need human assignment to ensure they get addressed.
The bystander effect in code#
When a security alert affects everyone, it often gets fixed by no one. It’s the digital equivalent of watching someone need help in a crowded room—everyone assumes someone else will act.
Personal responsibility changes behavior#
The moment a vulnerability becomes “yours,” the relationship changes. It shifts from background noise to personal responsibility.
Trust and delegation#
Security campaigns represent something profound about how we organize collective action. We can’t simply trust that important work will happen organically—we need systems that create clarity about who does what.
The evolution of security thinking#
This update reflects a maturation in how we think about application security:
From detection-centric to remediation-centric#
Old thinking: “We found 1,247 vulnerabilities!”
New thinking: “We fixed the 12 that actually matter.”
From automated to human-centered#
Old approach: Let automation find everything
New approach: Let humans prioritize and own the important stuff
From individual to organizational#
Security campaigns acknowledge that meaningful security improvements require coordinated effort, not just individual vigilance.
What this reveals about software teams#
The need for explicit assignment and campaign management reveals something interesting about how software organizations really work:
Implicit vs explicit coordination#
Teams often assume important work will naturally get done, but explicit systems consistently outperform implicit assumptions.
The motivation gap#
Finding problems is satisfying (look what we discovered!), but fixing them is often tedious. Assignment bridges this gap by making remediation someone’s explicit responsibility.
Collective action problems#
Security improvements benefit everyone but are costly to implement. Without clear ownership, they often don’t happen.
The thoughtful questions#
What does it say about our tools that we need human assignment systems? Are we acknowledging that automation alone can’t solve coordination problems?
How do we balance personal accountability with collective responsibility? When everything becomes someone’s specific job, do we lose the sense that security is everyone’s concern?
What’s the right ratio of detected vulnerabilities to actually fixed ones? Is it better to find fewer issues that actually get addressed, or cast a wide net and accept that most won’t be resolved?
Getting started#
Security campaigns for secret scanning are rolling out in public preview for GitHub Secret Protection or Advanced Security customers. Assignable alerts are available today for Code Security, Secret Protection, or Advanced Security customers.
Start with small campaigns focused on your highest-priority secrets or most critical code paths. Learn how your team responds to explicit ownership before scaling up.
The human element#
Perhaps the most interesting aspect of these updates isn’t the technology—it’s the acknowledgment that human psychology matters in security processes.
We’ve built incredibly sophisticated systems to find vulnerabilities, but we still need traditional organizational tools—assignment, campaigns, progress tracking—to ensure they actually get fixed.
There’s something beautifully human about needing personal ownership to solve collective problems. Maybe that’s not a bug in our systems—maybe it’s a feature of how we work together.
Learn more: Explore GitHub’s documentation on security campaigns and assignable alerts to set up coordinated security remediation for your organization.